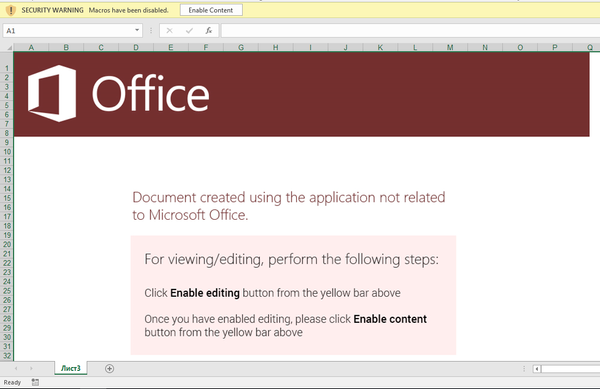
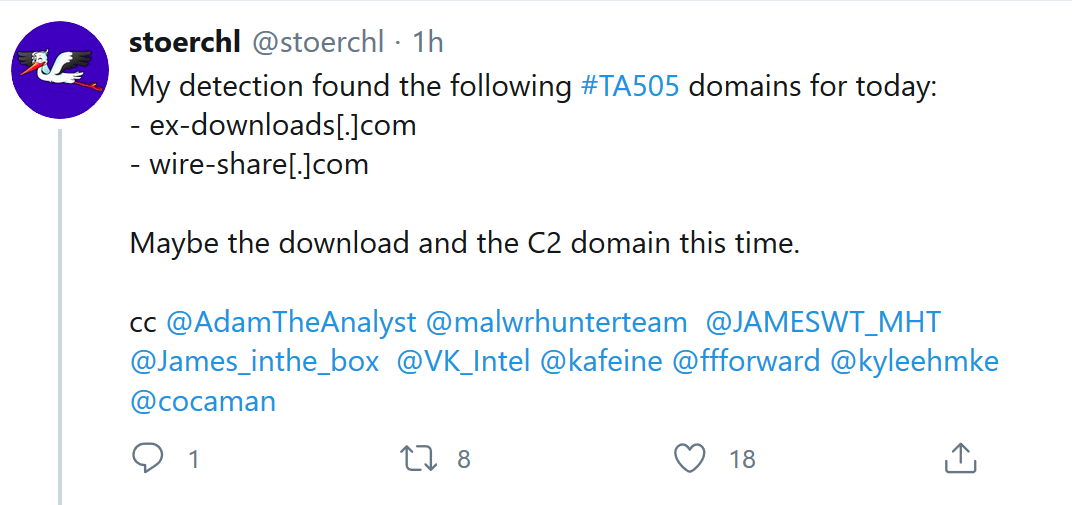
I am not your Regular #BlueTeam #YARA #Guru who is writing yara for everything everyday. But, was assigned for a task where I need to find-out a proper Yara for a specific class of new gen malwares where AV or SHA/MD5 based IOC's are not working. Even the network connections are to different domains as there are way too many variants ( Read about it more here ) . So, I gathered around 50+ samples of same kind virus, but with lesser or zero AntiVirus detection.
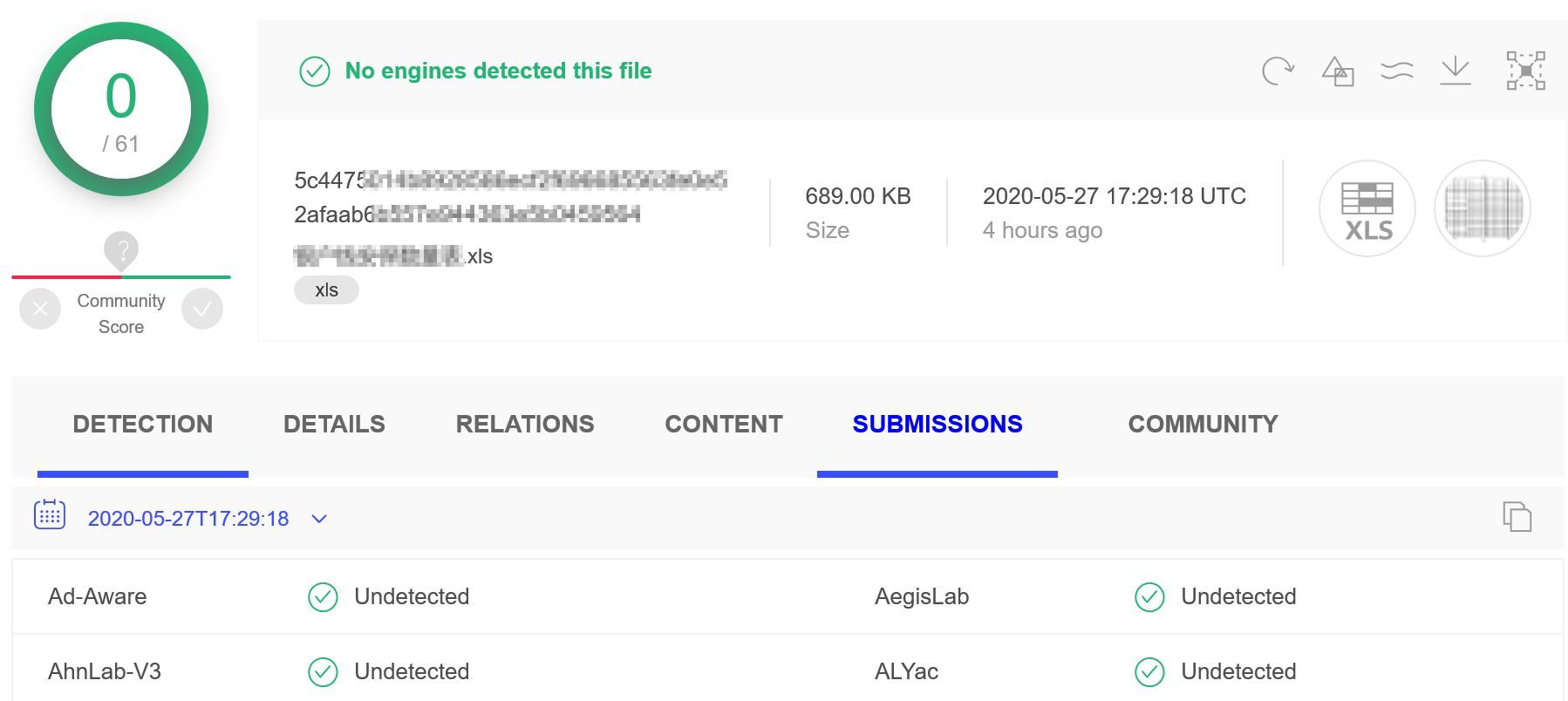
Then when went through YARA documentation, found that I can only block this by repeated pattern on each samples of same variant. And Yea ! you get it right - Binary Strings Never Lies !
But binary strings matching from more than 50 samples, where each files are 200kb to 900kb ! 🤯 Really tough job to get the patterns from an #undetectable. So, after few tries I came up with lazy man's way, but where you can choose actually what you want to put as a string atleast keeping a human flavour intact, but in a super fast way. 😎
Could have done with some spaghetti code, as I am not a regular coder. But, then thought why not coming up with a Sys Admin way, rather in a coder way. So, yea - #BASH is there for #Rescue.
#!/bin/bash
# YaraSilly2 ( a.k.a Yara Silly Silly )
# Automatically Builds Yara Rules From Malware Samples
# Just a Basic Scratch Script - Yet !
# Copyright 2020 Krishnendu Paul [email protected]
# Released under GPL3 Licence
for file in *;
do
strings $file > $file_tmp.txt
sed -i "s/ //g" $file_tmp.txt
awk '!seen[$0]++' $file_tmp.txt >> dump.txt
rm $file_tmp.txt
sed -i '/^$/d' dump.txt
done
sort dump.txt | uniq --count --repeated | sort > results.txt
sed -i '/^$/d' results.txtSo, put all your malware samples in a folder. Copy above script and save it to a file ( yarasilly2.sh ) . Then,
chmod +x yarasilly2.sh
./yarasilly2.shOne it is finished, just open results.txt .. and Voila ! ..
root@Bidhata-X1:/mnt/c/Users/me/Desktop/TEST# cat results.txt
2 ?.}
2 #}`-
2 &<>=
2 ((((((
2 ;{_+
2 =*?>
2 ?#}+
2 @[@~
2 @`@~
5 !"#$%&'()*+,-./01$
5 EFGHIJKLMNOPQRSTUVW$
5 XYZ[\]^_`abcdefghij$
8 \&0;
8 5RI]
8 7ay"+
8 9@"J
8 Administrator - Personal View`
9 Administrator
9 Calculation
9 Check Cell
9 [Content_Types].xml
9 [Content_Types].xmlPK
9 Excel 4.0 MacrosYou have a handy list with the count of string occurrence in total. Left column with number is the count of occurrence on those samples . So, more greater the number, more chances of lesser false positive. But yes, there can be regular strings as well, like for Excel files - keyword Excel obviously will be there ( Opps ! ) . So, I am living it to human part of you.
A Simple Yara Rules I generated for almost a non-detectable macro enabled XLS files which not yet have a false positive in VirusTotal live hunt.
// Excel files with macros pushing registry and downloading malware
rule macro_downloader
{
meta:
author = "KP - SwedBank"
description = "Malware Pushing XLS detection May 2020"
strings:
$meta_value1 = "##0\\)"
$meta_author = "Administrator"
$meta_app = "Excel"
condition:
all of ($meta_*) and filesize < 1MB
}
Do you want me to make it a more enhanced Poor Man's Yara Rules Creator based on Binary Strings ? May be, may be starting a project named #YaraSillySilly 🤫