Yes, it is a known story now that IT Giant #Congizant suffering from Maze Malare infection partly. Lot of their system got encrypted and hackers asking for Ransom !
There are other malwares, but one of the tactics used by Maze / ChaCha group to put pressure on their victim is to publish the data on the internet as leaked data. So, for a company like #Cognizant , who handles a lot of customers data - it is really business critical.
You can get the full detailed analysis my McAfee here https://www.mcafee.com/blogs/other-blogs/mcafee-labs/ransomware-maze/
I will share few of my findings which may give some extra informations. Now, lets move to technical details. Following are the files of the infector
| MD5 | SHA256 | NAMES |
|---|---|---|
| 910aa49813ee4cc7e4fa0074db5e454a | 4218214f32f946a02b7a7bebe3059af3dd87bcd130c0469aeb21b58299e2ef9a | kepstl32.dll |
| 76f8f28bd51efa03ab992fdb050c8382 | 5470f0644589685000154cb7d3f60280acb16e39ca961cce2c016078b303bc1b | memes.tmp |
| b6786f141148925010122819047d1882 | c84b2c7ec20dd835ece13d5ae42b30e02a9e67cc13c831ae81d85b49518387b9 | maze.dll |
| 11308e450b1f17954f531122a56fae3b | 9845f553ae868cd3f8d8c3f8684d18f226de005ee6b52ad88b353228b788cf73 | RANDOM |
You can download all samples from here.
Download Maze MalwareMessege me , or break the password to get the files.
Till date, I found around 8-9 variants of the same malware. If you remember , there were huge hit on multiple English Speaking farm , on last 2019 by the same group. Last time they disclosed a 14.1 GB file containing data from various organization in underground Russian forum. And, recently on 2020, they release around 9.5 GB of data from few companies related to health sector.
Last time they infected using spams and fake application. But, this time it seems hot topic #Covid19 based email phishing campaigns. But, this time they deployed more complicated attack and persistance behaviour, including infecting recovery boot image. ( https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-7/dd744280(v=ws.10)?redirectedfrom=MSDN )
boot.sdi = Windows Deployment System Image.
It is overwritting C:\Recovery\XXXXXX-XXXXX-XXXXX-XXXXX\boot.sdi in my case. So, once you are infected, if you want to use recovery image to restore your PC - it will infect you again. Also, there are traces it is adding something in adobe acrobat directory as well
%PATH%\AppData\Roaming\Adobe\Acrobat\10.0\JavaScripts\glob.settings.js
From behaviour, it seems it is exploiting following on a system
- Adobe acrobat
- Microsoft Office
- Adobe Flash
- Some mediaplayer - which is vulnerable on M4A and .FLV files.
- Recovery Imgaes
- RDP ( Remote Desktop )
- Firefox
- Chrome
- Internet Explorer
It is having debug pdb set to C:\Wuhan\Lab\coronashit.pdb . Previous version use to have different pdb path.
Also, it contains to resources ( already segricated as details.dll inside the zip file ) . And more confusing, in string table - having CHINESE HONGKONG as language. For note, previous community use to believe that it is from Russian Origin.
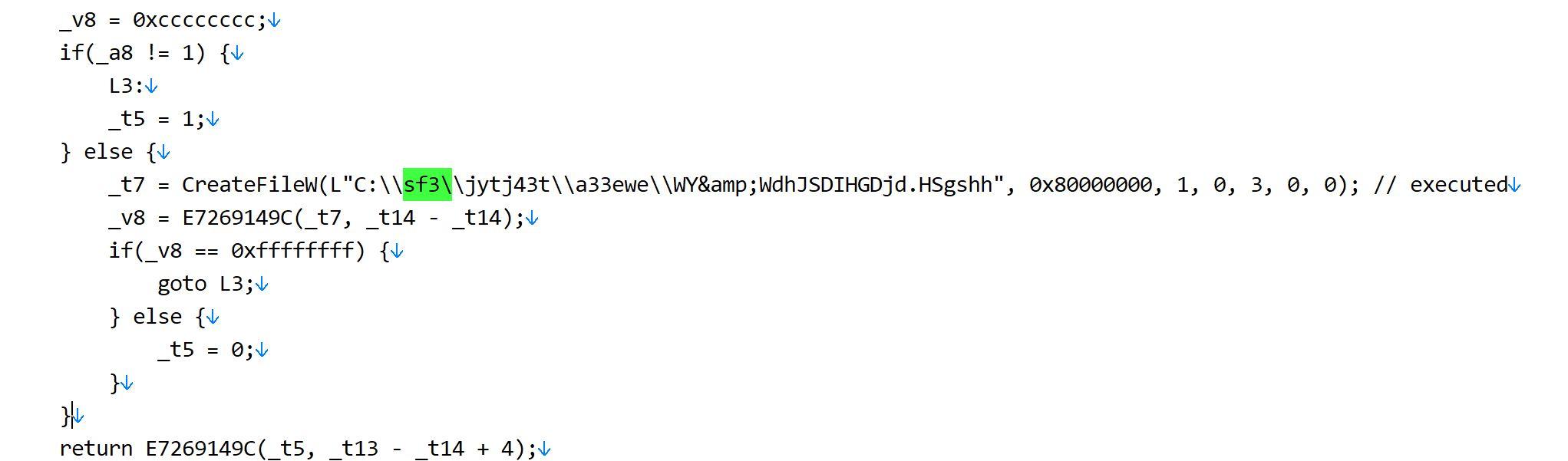
When going through the reversed code, came accross a section where it is checking for WY&WdhJSDIHGDjd.HSgshh file under C:\sf3\jytj43t\a33ewe\ folder and then exiting. Even if some researcher are pointing that as Kill Switch, but in my case it is not working, and also my thought is, it kept for a future version for something.
In static analysis it is on following Mitre Techniques
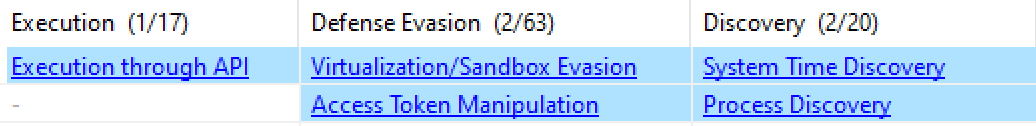
But, on dynamic analysis - actual game starts. It is having tremendous sandbox bypassing features included. It is waiting for more than 3 minutes before starting payloads. Also having debugger bypass as well. It is checking for CPU temp, system time etc.
MITRE ATT&CK MATRIX
Total URLs found on all version of Maze Malware including latest variants: https://transfer.sh/11px20/List of domains associated with Maze.txt
And if you need PCAP of network activities, here you are: https://transfer.sh/BhNtv/dump-c043c153237b334df2f2934f7640e802.pcap
It also delete all shadow copies
C:\Windows\System32\wbem\WMIC.exe 'C:\assa\pcccc\..\..\Windows\ncd\..\system32\grkn\wpxrq\..\..\wbem\bbup\ott\yf\..\..\..\wmic.exe' shadowcopy deleteI am very confused about lateral movement once they infected one system inside #Cognizant. I didn't found any wormable exploit inbuild, only RDP and share folder access bruteforce and password dumping !! It can not be a good reason for smooth lateral movement inside a company like #Cognizant have more than 200,000+ employees worldwide. Then - I found following. As per my source, forum thread opened on 11th April, 2020 and then closed on 15th April, 2020. And then Cognizant Incident happened.
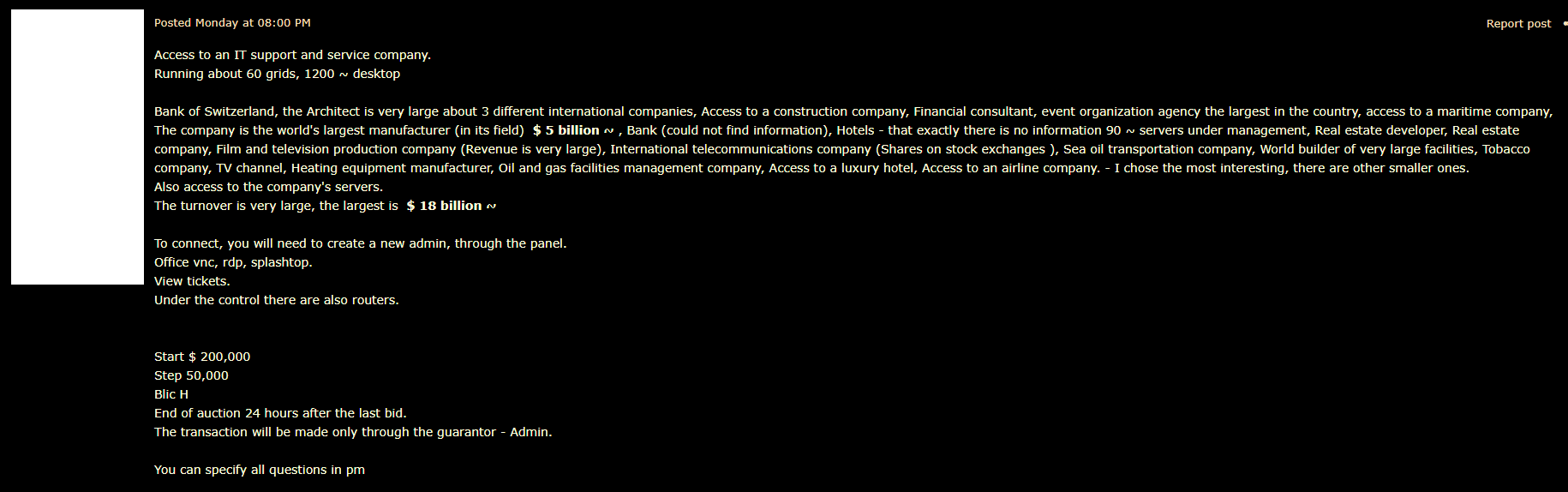
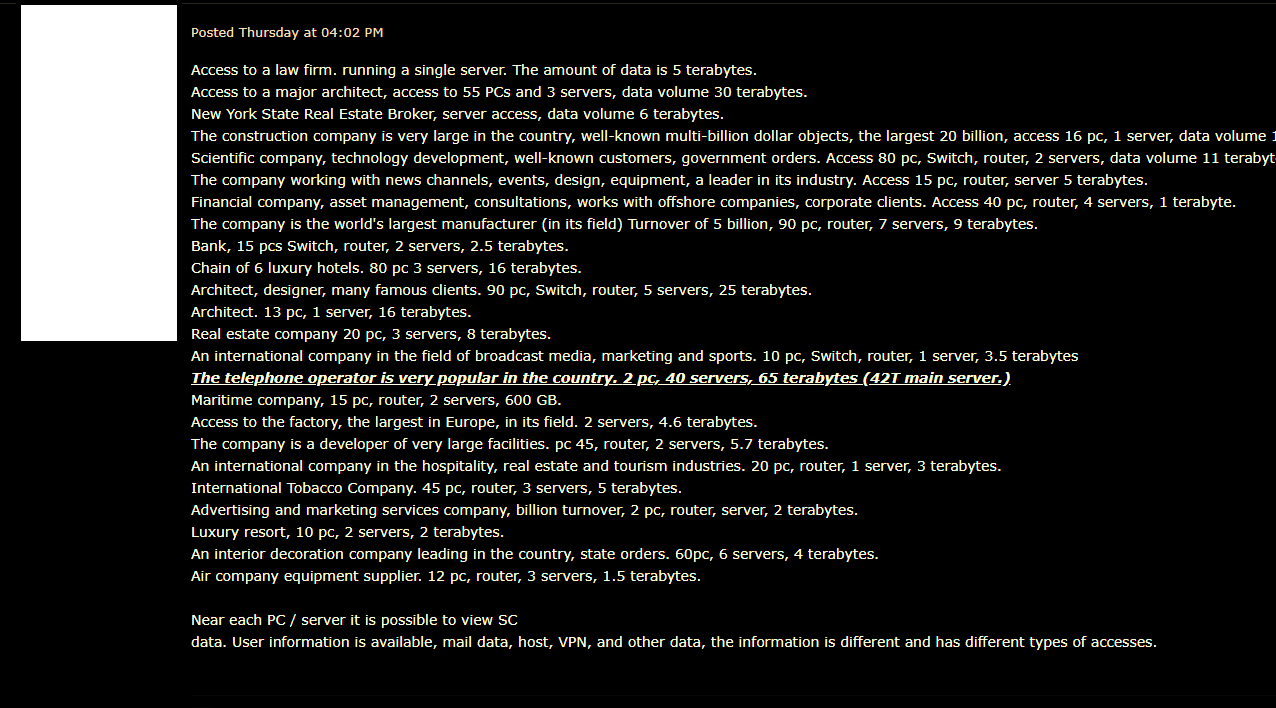
Is it the same company ? What do you think ? Please let me know in comment !
Seems they are exploiting following vulnerabilities for privilage escalation:
- CVE-2016-7255
- CVE-2018-8453
URLs accessed using POST
http://91.218.114.4/withdrawal/jfmd.do
http://91.218.114.11/view/messages/ugihhabxg.jspx?ar=0l868b71x
http://91.218.114.25/ex.action?gd=v5qh8a
http://91.218.114.26/post/account/eifxupy.aspx?e=p45ph1k&xen=j030&jxq=x&qe=4h78 http://91.218.114.31/lecfefe.jsp?ac=uqt38c3
http://91.218.114.32/rcqncstrcq.asp?xa=u&hgnt=883&e=y0hpt3n06c&a=e
http://91.218.114.37/support/check/is.aspx?y=ndf
http://91.218.114.38/aixffpqds.html?hdnw=72lr15&es=lwm7u8&tulq=6a43xi8
http://91.218.114.77/news/withdrawal/iku.jspx
http://91.218.114.79/sepa/ticket/idjyo.jspx?eri=wfb6bb2sr
As per my intel "encrypted computer keys are hidden inside NTFS metadata, by using Extended Attributes. An empty file is created, %ProgramData%\0x29A.db and a custom extended attribute named KREMEZ is set to that file" . Even if that's the decryption key, you need private master key to decrypt that key.
Advertisement:
GPUs offer computing at many magnitudes faster than CPU, whether it's for Machine Learning, Deep Learning, or other AI workloads. Rent GPU instance from RunPod and start your AI journey. TensorFlow, Pytorch, Jupyter and many other software available.