Few days back received a malware , which is more than 800MB in size. 1st time I ever seen this big malware file. When zipped, file size is 10-12 MB, and when unzipped, the filesize is more than 800MB.
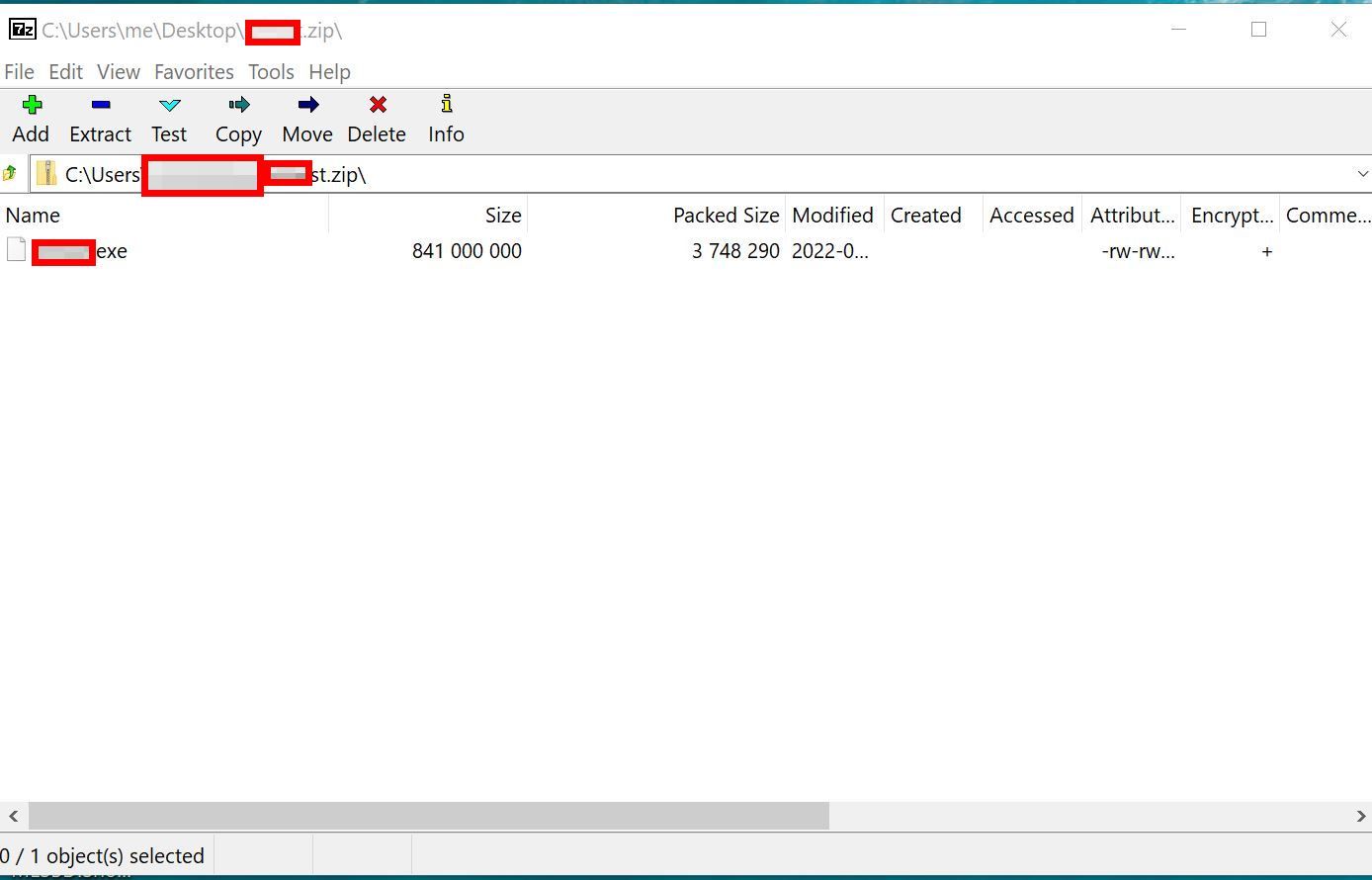
So, when I tried to execute it for dynamic analysis in any Sandbox - it failed to detect. ( Big sized file are not scanned due to resource limitation in Sandboxes ).
Tried to get the entrypoint for the binary, to findout the actual exe using PEStudio, but seems it failed. Maybe because of the size or Fake Entry point. So, now time to trigger old and trusted x64dbg
So, load the binary into x64dbg debugger, and click on Run.

Yes - the entry point. But, seems it is not original Entrypoint ! Hmm...
[Update]
Don't want to go through the tedious process to dump the binary from memory , but pointer is to findout EBP and ESP - just wanted to give an easier method I found later which works most of the time to extract actual PE from the packed file.
So, here comes the life save from Didier Stevens utility - named "pecheck" . It is a tool for displaying PE file info . But, it is having a special feature to dump the PE from the packed file. So, the syntax is following.
pecheck -l 1 -g s -D sample.exe > unpacked_sample.exeYea - that's it !!!
( And I wasted 2 days to get the correct Entrypoint to dump the file from memory.) Thanks for the tool Steven. Life saver.

